As more companies make the shift to the cloud, concerns around data privacy and compliance are more prevalent than ever. While many see the benefits of moving their workloads to the cloud, those in heavily regulated industries such as financial services and healthcare need the protection controls that help safeguard sensitive IP and regulated data wherever it resides.
Confidential Computing, the protection of ‘data in use’ is one of the critical means of protecting data and apps in the cloud. Both Intel and Microsoft were founding members of the Confidential Computing Consortium, which was created to move this area of secure computing forward through investments in technology and expanding the ecosystem. Azure confidential computing recently released a new VM DCsv3 featuring Intel SGX technology that helps protect data in use with a hardware based Trusted Execution Environment.
Watch this episode of Microsoft Mechanics with Intel’s Mike Ferron-Jones and host Jeremy Chapman to learn more about Microsoft’s work with Intel to protect the most sensitive information in the Cloud, unpacking the latest silicon level, Zero Trust protections and the types of attacks they defend against, as well as the confidential computing scenarios that are now possible, such as machine learning analytics on multi-party data and more.
The bottom line. When it comes to Zero Trust principles, even your cloud service provider shouldn’t be inside your trust boundary. Azure provides a secure environment where your data is protected at rest in their datacenters and encrypted while it’s in transit. Azure Confidential Computing takes it a step further, by protecting your highly sensitive “data in use”, and you can retain the encryption keys. Which is good news if you are from a highly regulated industry or have privacy and compliance concerns over where your data is stored and how it is accessed by apps, processes, and even human operators.
Silicon plays an integral part in Zero Trust defenses, and, at Intel, we’ve spent almost two decades creating hardware-based security innovations. These include the protection of data held in memory, as well as protections for data actively in-use during compute operations in places like the Azure cloud.
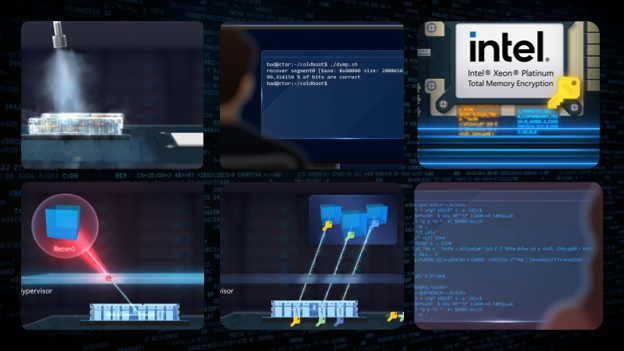
Total Memory Encryption. The latest generation Intel Xeon Scalable Processors are equipped with a technology called Intel Total Memory Encryption (TME), which helps to protect the data stored in memory with a unique hardware-protected encryption key from events such as a “cold boot” attack. The Xeon memory controller encrypts data as it is written to the DIMM so, even if the data is dumped, none of it is readable.
Total Memory Encryption Multi-Key. To layer on another level of defense, Azure has implemented the Intel Xeon Processor’s Total Memory Encryption Multi-Key (Intel TME-MK) capability. Like Intel TME, Intel TME-MK encrypts data held in memory, but instead of a single master key, Intel TME-MK uses VM-specific keys for each of the tenants on the platform. Even if an attacker was able to compromise another key or penetrate the hypervisor’s page table separations, it could retrieve only cyphertext from another VM’s memory region.
Software Guard extensions. To help protect sensitive data in use, Intel developed Intel Software Guard extensions or SGX, that creates protected areas of the CPU and memory - called an enclave - designed to allow only verified, trusted code to process confidential data. Microsoft built the Azure Confidential Computing DC series virtual machines which leverage these silicon level innovations.
Intel SGX helps to mitigate against some of the most difficult to defend against attacks such as privilege escalation attacks - These are most commonly software-based attacks where low-privilege code exploits vulnerabilities in high-privilege software to gain deeper access to data, applications, or the network.
It's designed such that any software running outside the enclave can’t see the data and code inside. Even if it has escalated its’ privileges, it’s just not trusted. That includes any other applications, the operating system, hypervisor, even the VM and cloud administrators. In fact, Intel SGX has the smallest trust boundary of any Confidential Computing technology for the data center today!
Watch the full Microsoft Mechanics episode to learn more about the different use cases on ways different organizations can work together on shared datasets in multi-tenant, public cloud services, without compromising security or privacy.
Learn More
- Learn about Azure confidential computing
- DCsv3 and DCdsv3 are now generally available
- Documentation for DCsv3 and DCdsv3 Azure Virtual Machines
- Learn more about Intel Memory Encryption Technologies and Intel Software Guard Extensions
Notices & Disclaimers
- Intel technologies may require enabled hardware, software or service activation.
- No product or component can be absolutely secure.
- Your costs and results may vary.
- Intel, the Intel logo, and other Intel marks are trademarks of Intel Corporation or its subsidiaries.
- Other names and brands may be claimed as the property of others.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.