Comprehensive Security Starts with Intel – Yesterday, Today and Tomorrow
Security has been a major focus for companies across industries over the years. With business-critical assets from hardware to data at risk of attack, leaders understand the long-lasting impact security breaches can have on the business. Intel’s commitment to security has never been stronger. We invest in unparalleled people, processes, and products, integrating security in the ways we work and everything we build. We relentlessly pursue the best solutions to help protect customer systems and data. For over 40 years Intel has been committed to building the most secure hardware on the planet, because if hardware isn’t secure, then the applications and technologies running on them cannot be secure either.
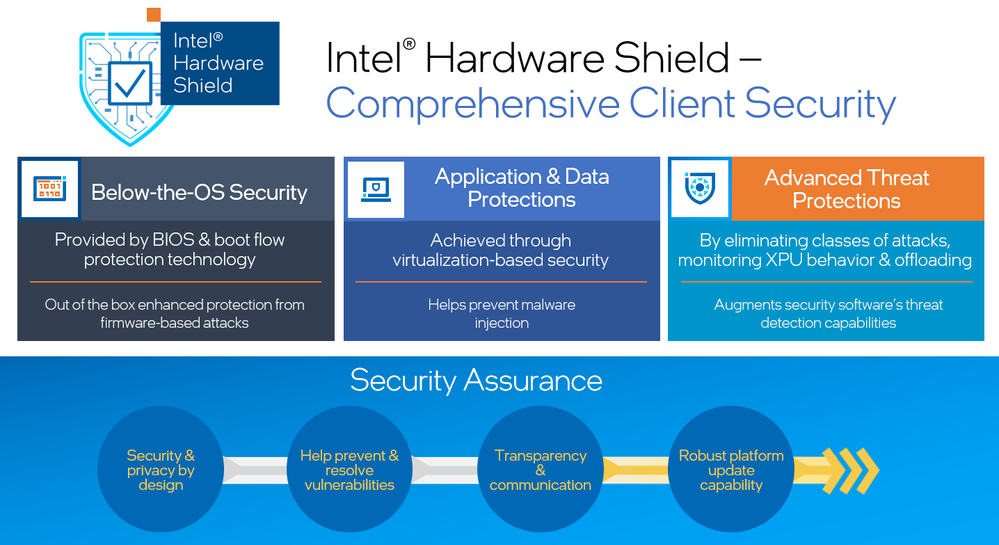
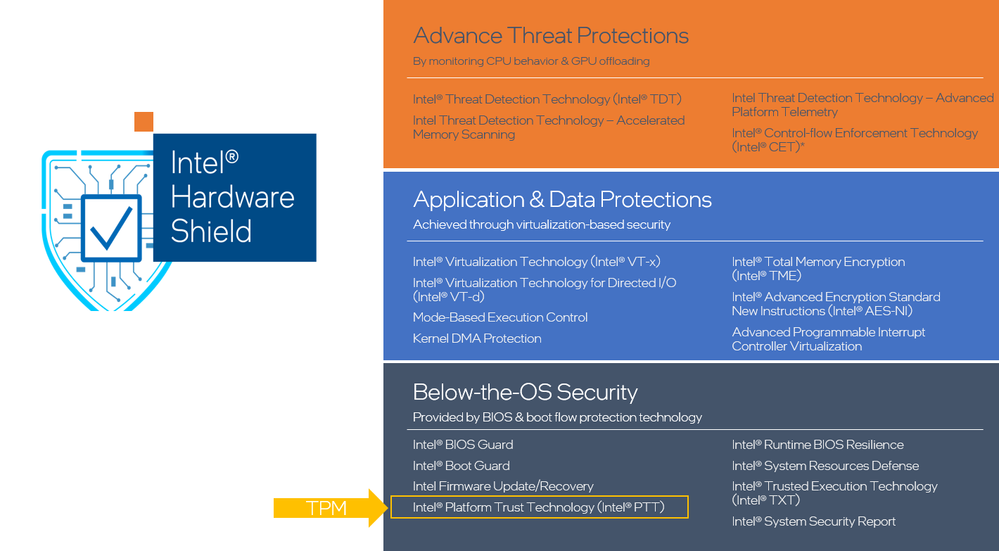
Intel takes a comprehensive approach to security. There’s no panacea. Our client products offer a collection of defense-in-depth capabilities delivered out-of-the-box. These capabilities help protect below the operating system, within the operating system, as well as deliver a hardware optimized threat detection capability for the latest ransomware and cryptojacking attacks. Our teams tirelessly innovate in security on each platform we deliver, in an effort to further reduce the attack surface for our customers and partners.
Our holistic security approach extends to our partner networks. Intel’s silicon and platform technologies are the foundational building blocks for the products our partners build upon, like original equipment manufacturers (OEMs), operating system vendors (OSVs), and independent software providers (ISVs). Inclusion of our partner network in maintaining a strong and resilient security posture is crucial and allows us to deliver choice for our customers.
The Value of an Open and Diverse Ecosystem
In a diverse ecosystem, an open approach to security fosters the best security outcomes. And tomorrow’s cybersecurity challenges require a comprehensive portfolio of offerings that can meet these challenges, while also satisfying the evolving needs of our business and personal computing customers. By working together, through this ecosystem, we can tackle the toughest security challenges facing our customers, while also expanding the range of technology choices available to them.
Whether it is delivering the recently announced Windows 11 PCs or Chromebooks, we work closely with our partners to enable our customers to use their device of choice to delivers an experience they demand and the security they need.
Security is all about trust, and trust is rooted in transparency. To this end, Intel has developed an inclusive, transparent, and shared vision for security that enables a framework for innovation. The success of this framework is due in large part to the diverse ecosystem of technology contributors and partners we support, and the level of collaboration that we encourage from all participants.
Intel’s Integrated Trusted Platform Module
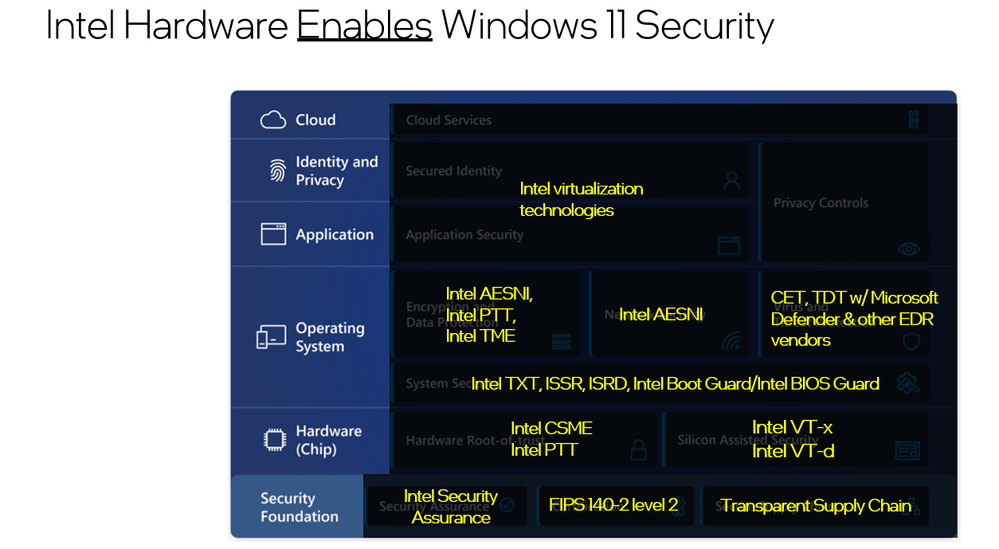
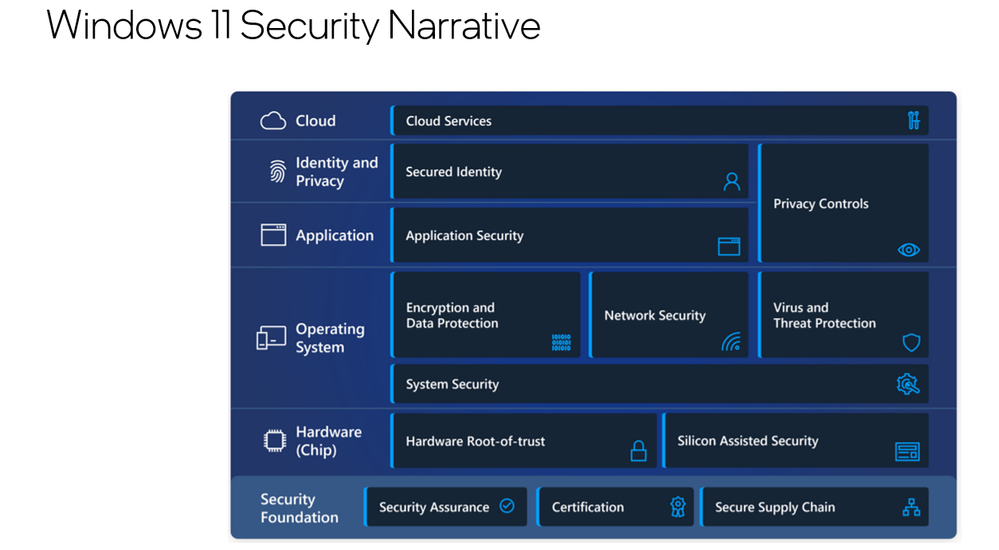
Intel® Converged Security and Management Engine (Intel® CSME) is the silicon root of trust, integrating security features into the processor and chipset. This tight integration, implemented in our own Intel platform security technology, provides performance and cost-optimized security capabilities that help eliminate vulnerabilities while improving the overall user experience.
And while we expect discrete TPMs to continue to have an important role in Windows-based PC platforms, there are emerging cybersecurity needs that are driving our OEM and OSV partners to look beyond the traditional requirements met by the discrete TPM and push root of trust further down into the chipset. Intel envisions an increased need to support the emerging root of trust requirements of our OSVs and OEM partners, including the Windows, Chrome OS and Linux-based environments. For example, our OSVs are engaged in root of trust efforts, such as Google’s Open Titan and Microsoft’s Pluton TPM Technology. Our OEMs also offer innovation around their own hardware security offerings. Intel collaborates closely with all our partners to offer a comprehensive set of security capabilities that continuously raise the bar for security with Intel platforms.
Choose the right TPM type for your use case
Learn more about Intel Trusted Platform Module
Through our focus on security and innovation, we are building a future that supports our partners’ independent root of trusts, enabling them to coexist and interoperate with confidence on our platforms, today and well into the future.
Intel Is the Foundation that Will Drive the Future of Security
We are proud to offer Intel platform security as the defensive bedrock beneath the technologies that support leading businesses around the world. Our commitment to building a secure future fuels our engineers and partners as they work together on the toughest security issues of tomorrow, while striving to protect our customers today. Intel’s rich history in hardware gives the world's leading businesses a security foundation deeply rooted in the silicon itself, with a fundamental principle of customer choice.
Notices & Disclaimers
Performance varies by use, configuration and other factors. Learn more at www.Intel.com/PerformanceIndex.
Performance results are based on testing as of dates shown in configurations and may not reflect all publicly available updates. See backup for configuration details. No product or component can be absolutely secure.
Your costs and results may vary.
Intel technologies may require enabled hardware, software or service activation.
© Intel Corporation. Intel, the Intel logo, and other Intel marks are trademarks of Intel Corporation or its subsidiaries. Other names and brands may be claimed as the property of others.
 Michael Nordquist is the Vice President Client Computing Group & General Manager, Business Client Product Planning and Architecture. He has overall product planning and architecture responsibility for Intel’s business client platforms, including the Intel® vPro™ brand, across all desktop and mobile platforms. Nordquist has held a variety of sales, marketing, planning, and management roles since joining Intel in 2000. Prior to running product planning for the Business Client Group, he was the director of strategic planning focused on phones, tablets, and our Intel® Atom™ microprocessor. He holds a bachelor’s degree in electrical engineering from the University of Minnesota and an MBA from Babson College.
Michael Nordquist is the Vice President Client Computing Group & General Manager, Business Client Product Planning and Architecture. He has overall product planning and architecture responsibility for Intel’s business client platforms, including the Intel® vPro™ brand, across all desktop and mobile platforms. Nordquist has held a variety of sales, marketing, planning, and management roles since joining Intel in 2000. Prior to running product planning for the Business Client Group, he was the director of strategic planning focused on phones, tablets, and our Intel® Atom™ microprocessor. He holds a bachelor’s degree in electrical engineering from the University of Minnesota and an MBA from Babson College.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.